|
Summary: Companies that can provide quick and robust authentication mechanisms will be in a strategically important position in the digital economy, and this is sparking an arms race among the major Internet ecosystems – Apple, Google, Facebook and Amazon. This race is intensifying as biometrics and wearables promise to make two-factor authentication easier and more cost-effective. What are the strategies of the internet players, and where do they need help? (May 2015, Dealing with Disruption Stream) |
|
Below is an extract from this 44 page Telco 2.0 Report that can be downloaded in full in PDF format by members of the Dealing with Disruption Stream here.
For more on any of these services, please email / call +44 (0) 207 247 5003.
To reduce both fraud and friction, the major brokers of digital commerce, including Google, Apple and Facebook, are all trying to develop authentication mechanisms that are reliable, secure and easy-to-use. For these Internet players, enabling effective authentication (both for their own services and within the broader ecosystem) is strategically important for four major reasons:
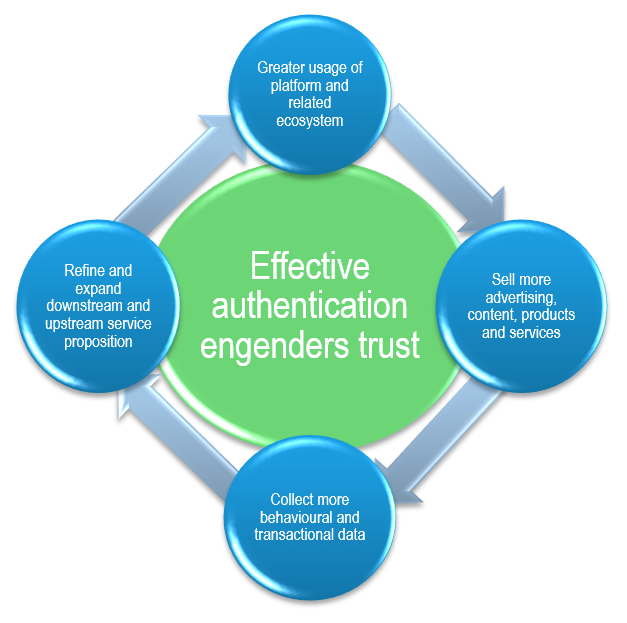
In essence, for the major Internet players, fast and secure authentication oils the flywheel at the heart of their two-sided business models, enabling the wheel to spin quicker and gain more momentum. Effective authentication mechanisms also engender trust, stimulating greater usage of the platform and the related ecosystem, encourages sales and gathers data, all of which can be used to refine and expand the core service proposition (see Figure 1).
Despite its strategic importance, the major Internet ecosystems haven’t yet perfected authentication. As building scale is usually the prime strategic imperative, most Internet players put ease of use ahead of security and verification. They, therefore, don’t fully verify the profile information, such as gender and age, provided by consumers. Facebook, for example, is used by large numbers of pre-teen children claiming to be 13 years old – the minimum age to use the service. In other words, Facebook’s identification process, which precludes the authentication process, is open to abuse.
Moreover, digital commerce brokers can’t always be sure that consumers are using a payment card that belongs to them. Apple has ended up refunding parents whose children used the payment cards associated with their parents’ iTunes accounts to make large numbers of in-app purchases.
Source: STL Partners
The leading digital commerce brokers want to be able to track consumers’ activities well beyond their own ecosystems, so they can better target ads and marketing messages through their ad networks. Facebook also appears to earn some revenue by selling third party web sites and apps profile information about people who log into their services using its Facebook Connect authentication mechanism.
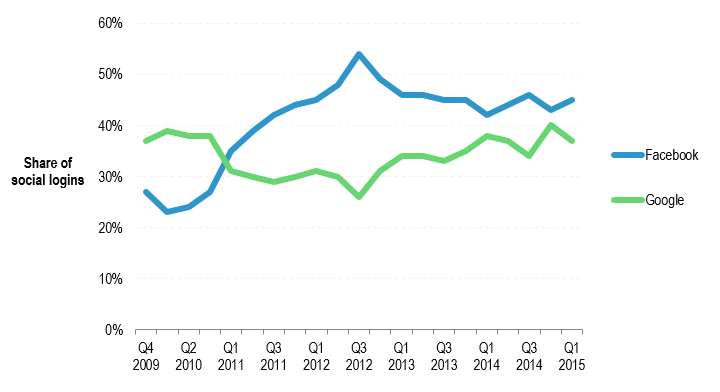
Over the past five years or so, Facebook and Google have been slugging it out to be the leading provider of authentication services to third party web sites (see Figure 2). Facebook overtook Google in late 2010, according to figures from provider of customer identity management technology Janrain, and then built up a big lead in 2012. However, over the past few years Google has clawed back some market share as its push to persuade consumers to use a single identity across all the Google services, including Search, Gmail and YouTube, has gained traction.
Janrain, which claims to track social login trends across tens of thousands of web and mobile sites, attributes Facebook’s strong performance in the first quarter of 2015 to the social network’s adoption of a more consumer-friendly approach, which gives users more control. “As of March of this year, all sites have been migrated to the new app version that features an anonymous login option and line-by-line sharing controls,” Janrain notes.
In the run up to the launch of the new authentication app, Facebook asked web sites and apps to explain why they’ve chosen to collect certain pieces of customer information in their data payload. Facebook said it would deny access to information if it deems the company’s rationale insufficient. This move reflects Facebook’ changing business model. Rather than focusing on selling third parties consumer profile information, Facebook is increasingly concerned with building out its advertising network. If a consumer logs into a third party web site using Facebook Connect, Facebook can show a targeted advert, which is more likely to be clicked on than a generic advert earning both Facebook and the third party web site commission. This is also the business model that underpins Google’s authentication-as-a-service. In other words, both the advertising broker and the web site can benefit if a user logs in via the broker’s authentication service.
At a high level, Facebook and Google face little competition from other large social networks, such as Twitter (5% market share), Yahoo! (3%) and LinkedIn (3%). However, in some specific segments, these smaller players do have significant market share. LinkedIn is a major player in the business-to-business market, while Twitter accounts for 10% of media social logins, according to Janrain.
Source: Janrain
After years of over-reliance on user names and passwords, and subsequent data breaches, the digital authentication processes are now changing fast. One-factor authentication (reliance on something the consumer knows, typically a username and password) is being superseded by two-factor authentication (something the consumer knows combined with something the consumer owns) across much of the digital economy. Both the leading Internet players and major telcos are employing hardware to try and make authentication processes more secure. Bluetooth beacons, NFC (the short-range wireless technology Near Field Communications), biometrics and smart watches are among the technologies being used in conjunction with mobile phones and/or SIM cards to authenticate individuals both in-store and online.
Apple is at the forefront of the charge to use new hardware and biometrics, specifically fingerprint recognition, to enable three-factor authentication, which combines something the user knows, with something they own and something they are. By positioning itself as a trusted custodian of consumers' identities and data, the iPhone maker is laying down the gauntlet to Google, Facebook and Amazon, which have largely relied on username/password combos, bolstered by fraud-detection algorithms.
However, fingerprint recognition, which is also being introduced by Samsung into its high-end smartphones, is unlikely to be the last word in biometrics authentication. Fingerprints can be reproduced as high-resolution photos and security websites have reported that Apple’s TouchID system has been hacked.
Some banks, such as Halifax in the UK, are testing heartbeat recognition systems, which work like this:
The next section considers how these new technologies could change the way people are authenticated in several key scenarios.
To access the rest of this 44 page Telco 2.0 Report in full, including...
...and the following report figures...
...Members of the Dealing with Disruption Stream can download the full 44 page report in PDF format here. Non Members, please subscribe here. For other enquiries, please email / call +44 (0) 207 247 5003.
Technologies and industry terms referenced include: APIs, big data, business models, digital commerce, Internet of Things,
localized commerce, location based services, mobile advertising, mobile commerce, mobile marketing, mobile wallets,
personal data, smart homes, Smartphones, SoLoMo.